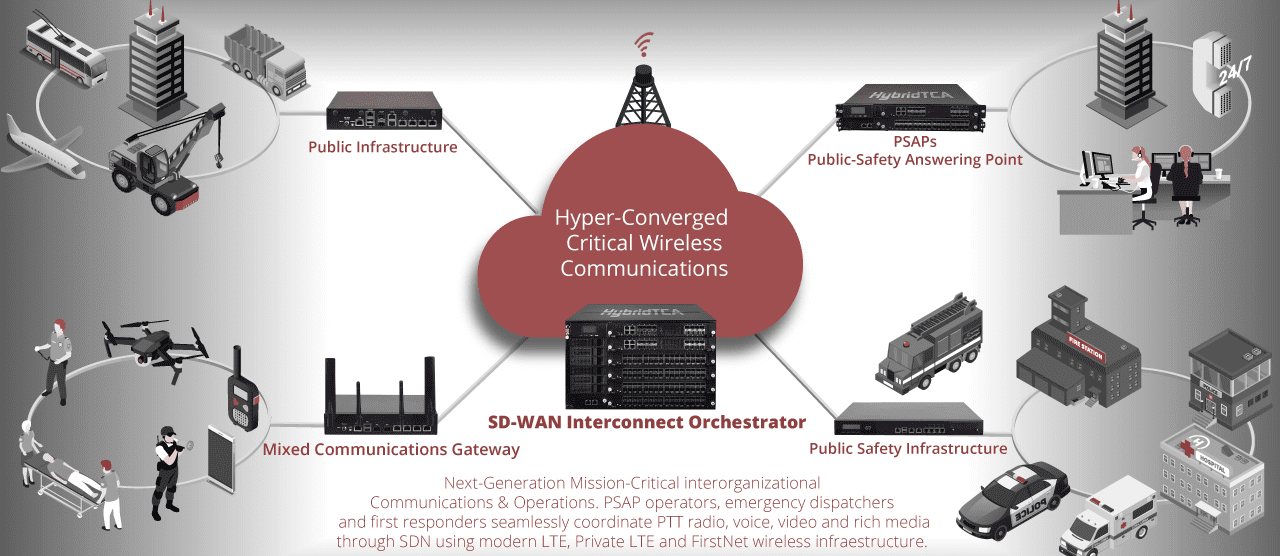
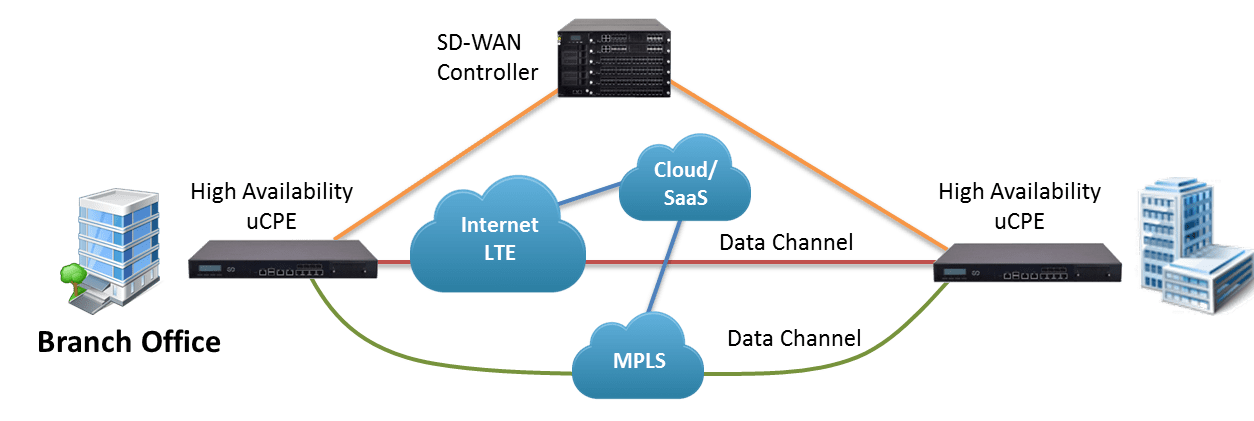
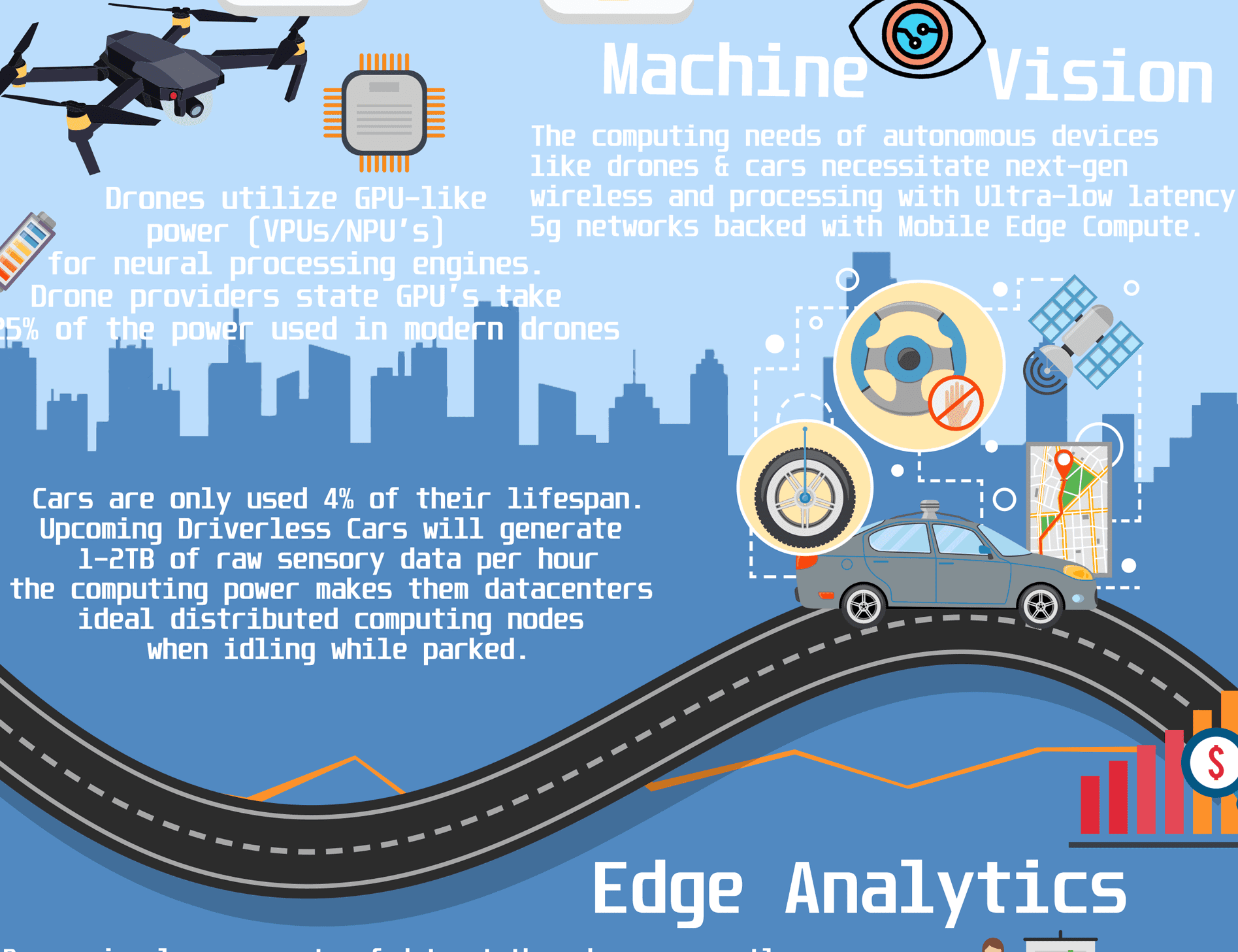
Rugged Industrial IoT Gateway for ICS/OT Security
In 2018, the U.S. Cybersecurity & Infrastructure Security Agency released a report (Alert-TA18074A) describing a Russian hacking campaign to infiltrate U.S.’s critical infrastructure, including power plants, nuclear generators, and water facilities. Hackers could have disrupted or shut down power plants or other critical U.S. infrastructure, but they didn’t take it that far. According to UtilityDive, …