Today we live in the age of impending danger for every device capable of interfacing with the internet. Ingenuitive malware, determined hackers and the ever-increasing attack surfaces present, not just in computers/phones, but the innumerable “smart” devices (IOT) has become a modern-day concern that has to be dealt with by the vast majority of individuals and industries. One of the most effective ways to deal with unknown cyber security threats is through the use of dedicated firewalls, designed to protect any & all devices on sensitive internal networks from external attackers or wrongdoers. However, truly effective firewalls need to consistently evolve and face new threats to businesses, organizations, processes and private individuals.
This is made increasingly difficult by the fact that these targets often possess little time, let alone the experience/resources necessary to implement & maintain a robust firewall security solution that best suits their requirements. Knowingly or unknowingly, everyone today has a device in their network that serves as a firewall between their devices and the internet, often provided by their Internet Service Provider (ISP). However rudimentary the implementation is, these firewalls still serve as an effective barrier to simple and constant attacks perpetrated by bots and motivated hackers. In this article we will take a look at the different implementations of firewalls, their effectiveness and use-cases in modern networks.
Stateful Vs Stateless – What’s the difference?
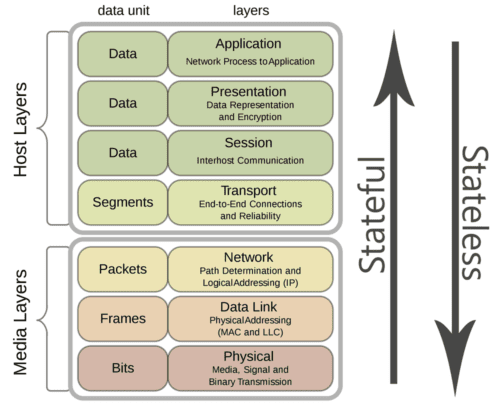
Stateless and stateful firewalls may sound pretty similar with being denoted with a single distinction, but they are in fact two very different approaches with diverging functions and capabilities. Packet filtering potential, is one of principle ways in which stateless and stateful firewalls differ from each other. While both firewall implementations perform packet filtering, the differences between them is in the methodology, depth and lengths they go to performing this function.
With these details in mind, well define the main distinctions between the two as this will help categorize and explain these implementations and the differences that exist between stateless and stateful firewalls. The main focus will be on how they compare to each other in terms of packet filtering performance, levels of security features offered and latent hardware requirements to run these functions. Let’s start off by understanding what both stateless and stateful firewalls are, what they are meant to do, and finally how stateless/stateful firewalls implemented as a solution compare in the real world.
Stateless Firewalls
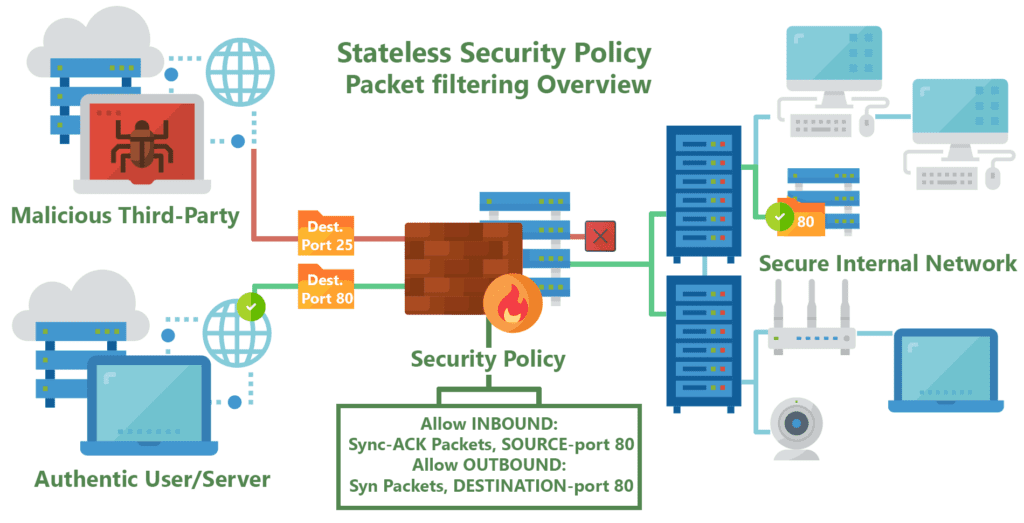
Stateless firewalls are some of the oldest firewalls on the market and have been around for almost as long as the web itself. The purpose of stateless firewalls is to protect computers and networks — specifically: routing engine processes and resources. They provide this security by filtering the packets of incoming traffic distinguishing between udp/tcp traffic and port numbers. The packets are either allowed entry onto the network or denied access based either their source or destination address or some other static information such as the traffic type (udp/tcp).These days completely stateless firewalls are far and few inbetween.
Today they are most commonly seen in the form of CPE’s (modems/router combos) given to customers by typical service providers. This equipment, usually given to residential internet consumers, provide simple firewalls using packet filtering and port forwarding functionality built on top of low-power CPE’s. Providing very basic but powerful security restricting incoming and outgoing traffic useful to protect commonly abused ports often by self-propagating or DDOSing malware, such as ports 443, 53, 80 and 25. This blanket port filtering is mostly implemented using white-lists allowing only a few key ports for application-specific traffic such as VoIP, as 90% of all internet traffic traverses with the Hyper-Text Transfer Protocol (HTTP) through proxy requests to Domain Name Servers (DNS). In other cases, such as when hosting servers for: multiplayer video games, email/web services, or live-streaming video, users must manually configure these firewalls outside of their default security policy to allow different ports & applications through the filter.
One commonly known pitfall of stateless firewalls is that they are unable to view packets as part of wider traffic and will inspect them in isolation and are mostly unable to distinguish the myriad of application-level traffic types (such as HTTP, HTTPS, FTP, VoIP, SSH, etc). This can make them susceptible to attacks that are not hidden within single packets but spread out across many of them. Stateless firewalls also do not keep track of the status of the network as a whole or the connections made to it. However, this does mean that stateless firewalls are much quicker and function more efficiently due to them only checking the header part of an inspected packet.
Stateful Firewalls
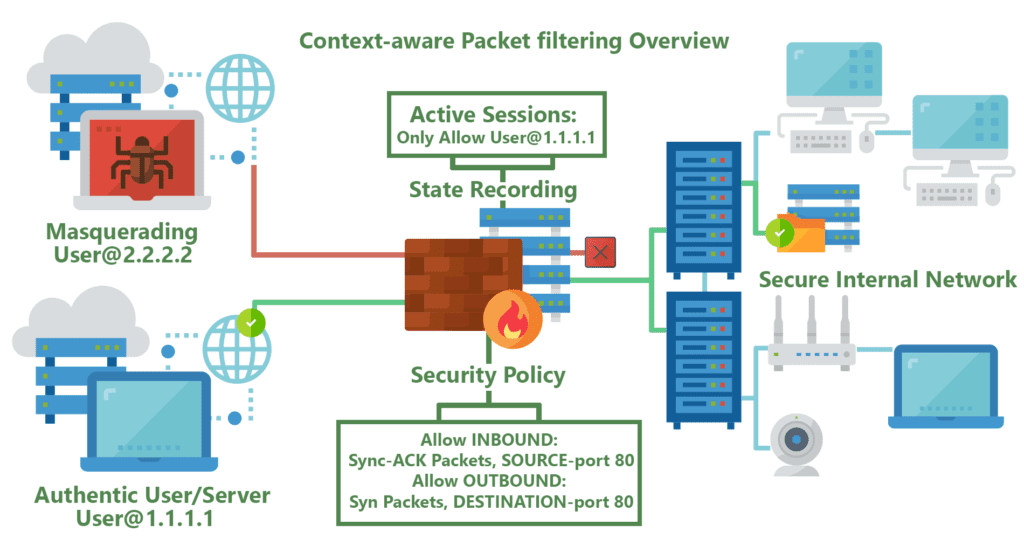
Most firewalls today offer at least some basic level of stateful monitoring. The main distinction between what can be very rudimentary stateful firewalls, and extremely robust packet-processing solutions, is in the level of protocol support. Greater support for differentiating between the diverse traffic and protocol types provides firewalls with the efficacy needed to analyze numerous application-level traffic, such as multimedia protocols, datagram protocols, file-transfer protocols, authentication/security protocols and so on.
Stateful firewalls are a more advanced, modern extension of stateless packet filtering firewalls in that they are continuously able to keep track of the state of the network and the active connections it has such as TCP streams or user datagram protocol (UDP) communication. The ability to acknowledging & utilize the context of incoming traffic and data packets is one of the principle advantages stateful firewalls have over their stateless cousins, allowing them to understand how to tell the difference between legitimate and malicious traffic or packets. This ultimately gives stateful firewalls one of the most powerful security tools in modern policies that protect their network connections through the implementation of additional security procedures for new or ongoing/active connections. In most cases, new connections will need to introduce themselves to the firewall with what most experts denote as a handshake, before being allowed onto the list of established connections.
Stateful firewalls are not without their vulnerabilities, however. The special handshake involved in establishing new active connections requires a significant increase in software/network connection complexity & the computational power needed to implement them, leaving such firewalls vulnerable to cyber threats such as distributed denial of service (DDoS) attacks. This threat has been mitigated by many users of stateful firewalls by spreading out a network’s traffic across more firewall appliances, with many using third-party cloud-based service middle-men, in order to reduce the risk and necessary infrastructure.
Which is better?
As is with most things, this varies on a case-by-case basis, with only the most basic residential users likely served well with their mostly stateless firewall given by their service providers. When it comes to power-users or business oriented networks, they are best served by the powerful stateful firewall implementations provided by dedicated systems running software such as PFSense, Endian or another robust offering. Having said this, while next-gen stateful firewalls offer all of the same security features present in stateless firewalls, they do not come without the need for cost-benefit analysis that should be done in regards to their feature-set and packet-filtering depth. The as important trade-offs and aspects of modern firewalls boil down to these requirements:
- Security Level (How secure/sensitive the information & network is)
- Performance Requirements (packets per second, devices on network, application overhead)
- Cost in terms of initial Capital Expenditure and ongoing Operating Expenditure for the hardware/software
- Networking & Computing Hardware Requirements along with the underlying infrastructure, space
- Software/Hardware Complexity, in terms of the integrations of upgradability, maintenance & support/EOL

For simple home use, modern computers have more than enough power to run robust software-based firewalls on desktop PC’s for example, but to easily secure the entire network using always-on purpose built low-power appliances like the NCA-1210 Edge Security Appliance is a more cost-effective solution. Much more stable as a whole, these dedicated appliances can be configured to consistently protect all home & handheld devices like smart thermostats/lights, IP cameras and smart phones from unwanted snooping/tampering by intruders – 24/7 while keeping maintenance, power, space and heat footprints to a minimum.
For more advanced usage such as small businesses, power users (online collaborators, home labs, tech enthusiasts, live-streamers) & larger entities, robust stateful firewalls are almost certainly the most viable option to protect sensitive user data, connections and active services. Here the heavier upfront cost of powerful hardware like the FW-8894 NGFW is less significant compared to the massive issues arising from the damages of lackluster security. Sub-par security can enable data breaches bringing issues such as: lawsuits, corporate/public image taint, service outages and contract/privacy breaches can all easily dwarf any upfront security investments.
Today businesses looking for the right security solution are best served by experts in the field of network security & hardware/software integration like Lanner. Capable of providing full services like validation, security module integration & quality assurance from the start – from the silicon & factory assembly all the way to the business premises.








