“Zero Day attack” is a phrase that has become increasingly more present in the public lexicon due to increased interest in cyber threats, partially down to the rise of the Internet of Things (IoT), but what exactly are zero day attacks? In the age of artificial intelligence, automation, and the Internet of Things, cyber-attacks are now, unfortunately, an everyday threat to organizations and society as a whole. There are varying different types of cyber threats, from man-in-the-middle attacks (MITM), whereby an attacker will intercept and access communications between two users without their knowledge, to distributed denial of service attacks (DDOS), where an attacker uses a botnet to target a single user system, flooding it with connection requests and malformed packets until it slows down considerably or crashes and shuts down.
What are Zero Day Attacks?
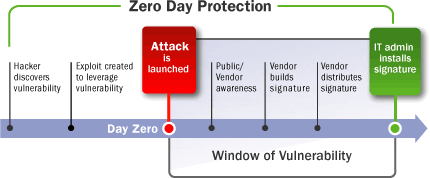
Zero Day attacks are cyber-attacks that occur before a vulnerability within software has been fixed. Usually, programmers and developers will try to keep their software’s vulnerabilities patched with regular software and security updates, however, sometimes these vulnerabilities become public knowledge before they can be fixed, exposing them to exploitation from malicious hackers. The term “zero-day” comes from the idea that developers and programmers have had zero time to look into and fix the vulnerability before it was exploited in an attack. Zero day exploits differ from zero day attacks in that exploits are usually vulnerabilities that have become public knowledge before their developers have managed to patch them, whereas zero day attacks are the actual attacks themselves. If a vulnerability is detected, programmers and cyber security officers tend to act quickly in order to protect both their users and their brand credibility or reputation, however, if a vulnerability has already been exploited, there isn’t too much that can be done to mitigate the damage.
Examples of Zero-Day Attacks
Over the years, there have been several high-profile examples of zero day attacks that have occurred in computer systems around the world. As you may already assume, any business or organisation that operates online is at risk from cyber-attacks, including zero day attacks. There are various reasons why hackers target specific brands, organizations, or locations, ranging from simply trying to be mischievous to full blown personal, corporate, or organizational data theft. Sometimes, hackers will target businesses or organizations that they are politically or ideologically opposed to in what has been termed “hacktivism.” Below are a few examples of zero day attacks.
Sony
Back in 2014, Sony Pictures Entertainment fell victim to one of the worst corporate cyber-attacks in history. A team of politically-motivated hackers known as the Guardian of Peace discovered a zero-day exploit in Sony’s network and used it to steal nearly 100 terabytes of data including the email addresses of senior executives, business plans, contracts, and four unreleased feature films.
Microsoft
In June of 2016, a cyber-criminal known as BuggiCorp began trying to sell a zero-day exploit on the dark web for $95,000. This zero day exploit apparently targeted a vulnerability in the OS’ local privilege escalation where attackers could then change any Windows level user account into an administrator account. In the original listing, BuggiCorp featured two videos of the exploit being used successfully, with one of the videos being right after ‘Patch Tuesday’, the day of the month when Microsoft usually releases its software and security patches. Whether the exploit was eventually sold remains as yet unknown.
Acrobat Reader
In February of 2013, a zero-day exploit was found in Adobe Reader 10 and 11 that bypassed the sandbox anti-exploitation protection within these two programs. Experts at Kaspersky Lab’s malware research and analysis team claimed that the exploit was highly sophisticated and was most likely a cyber-espionage tool created by a nation state or an interception tool from one of the many private contractors that provide law enforcement and intelligence agencies with lawful means of data and communications interception equipment. Tools such as this have been used before such as Stuxnet which was used to infect centrifuges at an Iranian nuclear enrichment facility.
DNC
The Democratic National Committee hack was one of the most widely covered cyber-attacks in history. The attacks started as a result of thousands of spear phishing emails being sent to targeted employees working for the DNC, rather than just out into the general public. The emails contained malicious links to phishing pages that, if clicked, would essentially hand over control of the user’s PC and the DNCs network to the hackers responsible. In total, 6 zero day exploits that where found and used by the hackers in operating systems and software including Microsoft Windows 10, Adobe Flash Player, and Java.
As we’ve now seen, zero-day attacks can cause a huge amount of damage if they are not dealt with swiftly and adequately. In many cases, zero-day attacks can be avoided through regular and thorough cyber security audits where the intention isn’t necessarily to pass without finding any, but to uncover as many potential exploits as possible and patch them over before they become public knowledge and can be taken advantage of. With the steady growth of the Internet of Things raising concerns over the protection of data in IoT devices, the future may see developers and programmers actively seeking out ethical hackers to test their systems in exchange for rewards. This could enable businesses and organizations to better protect themselves against these types of attacks in the future.







