Why do we need WAF and IPS security systems?
One of the most valuable assets (if not the most) of a company is its data. People who are dedicated to being “computer thieves” also know this, so they try different methods to attack a company network and access their valuable information.
The new types of sophisticated “hacking weapons” that carry out cyber-attacks have diversified so much that it is no longer enough to put a Firewall or just any NGFW (Next-Generation Firewall) at the edge of our network. Antiviruses have also played a key role in security for a long time, especially on the users’ workstations, but in the same case, they are not enough to stop crafty attacks.
A network administrator knows that this would be like locking the front door of our house but leaving all the windows and the back door open. Now that the attacks occur in different “layers” in the network protocols, for which we need different defense systems for each type of traffic. The fact that more and more companies have their permanent business in web applications can make them even more vulnerable.
According to the following chart from Statista, RIA’s companies are putting lots of investments in Cybersecurity. These companies manage assets of high net worth, so they need extra help in security.
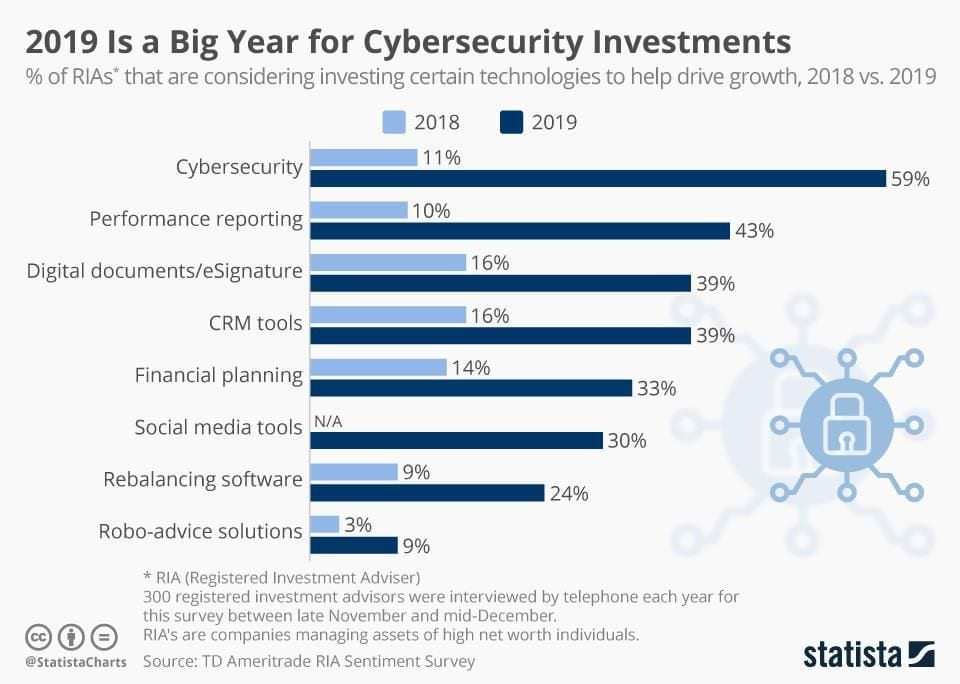
In an ideal world, the code of our web applications should not have any security “gaps” that can put us or our data on risk. But in reality, it is impossible to have 100% secured apps, so it is necessary to have external applications. Definitely, the more security barriers between ourselves and a hacker, the more peace of mind will be felt by business owners and website owners.
What options exist today to protect the servers (and even the data centers) of our companies from a large number of threats to our data?
Let’s talk about two options: Web Application Firewall (WAF) and the Intrusion Prevention System (IPS). What are the characteristics of each one? What do they have in common and what differentiates them? Which of the two gives more security to the network?
Web Application Firewall (WAF)
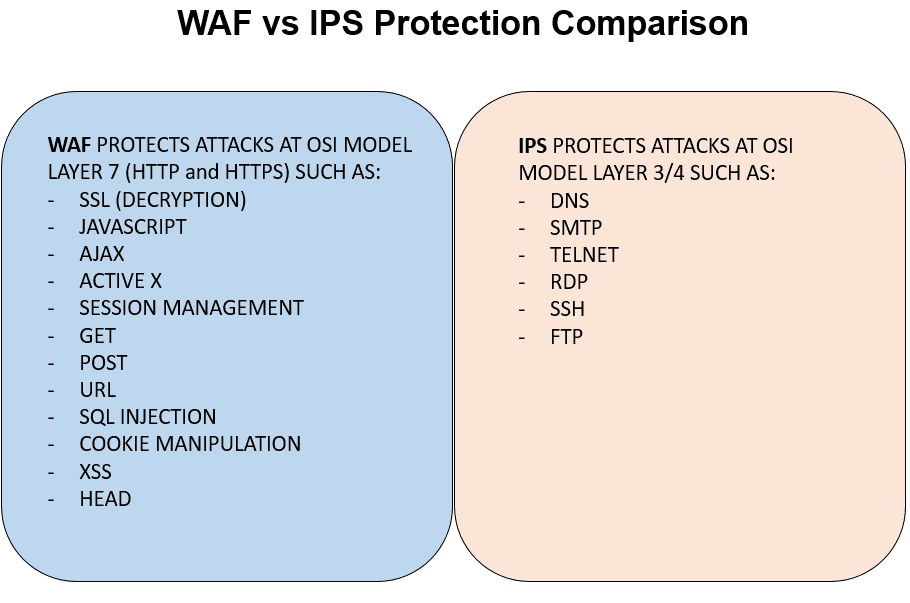
Web Application Firewall (WAF) is a solution (hardware or software) that works as an intermediary between external users and web applications. This means all HTTP communication (request-response) is analyzed by the WAF before reaching the web apps or users.
In order to perform the HTTP traffic monitoring and analysis, the WAF applies a set of previously defined rules that make possible the detection of malicious HTTP requests such as Cross-Site Scripting (XSS), SQL Injection, Dos or DDoS attacks, cookie manipulation, and many others.
Once the WAF detects a threat, it blocks the traffic and rejects the malicious web request or response with sensitive data. If there are no threats or attacks all your traffic should flow normally, in a way that all the inspection and protection are transparent to the users.
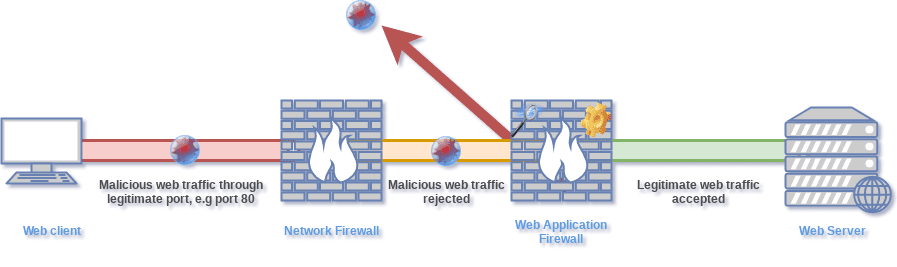
WAF recognizes legitimate web traffic and lets it through. It does not affect any day to day business web application operations.
Intrusion Prevention System (IPS)
In the case of the Intrusion Prevention System (IPS) is a more general-purpose protection appliance or software. It provides protection from traffic from a wide variety of protocol types, such as DNS, SMTP, TELNET, RDP, SSH, and FTP among others.
IPS detects malicious traffic using different methods, for instance:
- Signature-based detection: IPS uses signature-based detection just as an antivirus does. A firm can recognize a threat and send an alert to the administrator. For this method to work correctly, all signatures must be with the latest update.
- Policy-based detection: IPS requires that security policies be declared very specifically. The IPS recognizes the traffic that is outside of these policies and automatically rejects abnormal behavior or unusual traffic.
- Detection based on anomalies: According to the pattern of normal traffic behavior, this method can be used in two ways, either automatic or manual. The IPS automatically performs statistical analysis and establishes a comparison standard. When the traffic moves too far from this standard, it sends out an alert. The other way is by manually setting the normal behavior of the traffic so that alerts are sent when the traffic, again, moves away from this rule. The disadvantage of the manual way is that being less flexible and dynamic, it can send false alerts.
- Honey Pot Detection: Works using a computer that is configured to call the attention of hackers without compromising the security of the real systems. Using this bait, the attacks can be monitored and analyzed so that, once identified, they can be used to establish new policies.
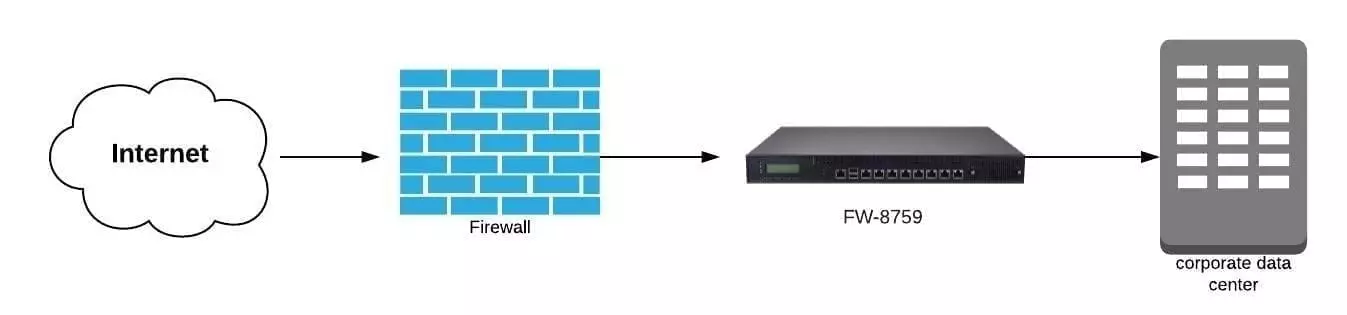
An IPS device can be used to improve security and support a firewall. As shown in the picture below, it blocks all abnormal traffic from the Internet, that wasn’t blocked by the first line of defense or the firewall.

Which one is my best option?
It is obvious that even both solutions add an extra security layer for our network, they work on different types of traffic. So, instead of competing, they mostly complement each other. Despite IPS seems to protect a wider type of traffic, there is a very specific one that only a WAF can work with. So, we highly recommended having both solutions, especially if your environment systems work closely with the web.
The below chart shows a quick comparison of both solutions.
Fortunately, nowadays there is the full package solution that gives you the best of both worlds.
The challenge is to select the right WAF hardware system to run software-based security mechanisms effectively. The most practical way to protect the enterprise data center from hackers is to implement a software-hardware or hybrid solutions.
When going for a web application firewall, consider the following requirements:
- SSL Acceleration: SSL is critical to WAF, as it is a CPU offloading method for the heavy-duty public key encryption. For optimal performance in your security implementations, it is recommended to have a hardware accelerator.
- DPI: Since the WAF is deployed between the enterprise server and the users, one of the major missions of the WAF is to monitor the traffic and block any malicious attempts. This requires an efficient DPI (Deep Packet Inspection) backed up by powerful hardware.
- High-performance and high-throughput: As DPI and SSL are both CPU-intensive, the required hardware architecture for WAF deployments must offer dedicated processing capability to run software securities.
- High-availability: WAF runs on a 24/7 basis and therefore, high-availability regarding power supply is critical to the optimization of WAF.
- Scalability: Since web application services may expand as the customer base grows, enterprise WAFs must be scaled up by hardware means in order to boost performance and accelerate critical applications in the simplest way.
Examples of WAF/IPS solutions
An integrated WAF/IPS security platform that comes with hardware acceleration can enable security algorithms for data encryption and decryption. This platform can target office routers, security appliances, UTM or Next-Generation Firewall appliances.
An example of this type of platform is Lanner’s FW-8759. This device is a mainstream, 1U rackmount network security system that uses the cutting-edge capabilities of the Intel Denlow platform (Based on Intel Haswell CPU and C226 PCH).
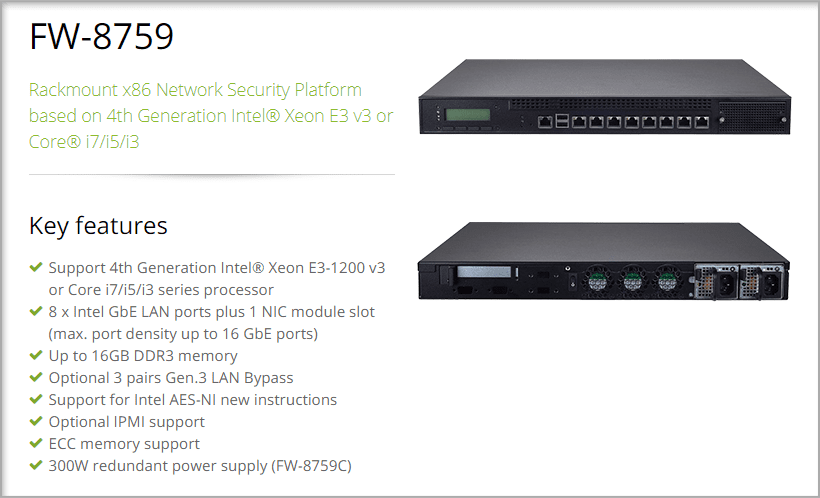
It features eight built-in Intel GbE LAN ports and 1 NIC module slot. This appliance can support maximum port density up to 16 GbE port, making it perfect for cybersecurity applications such as UTM, Firewall, VPN, IPS, and WAN optimization.
It is, indeed, powerful enough to be your company security shield at all levels.
Conclusions
Despite all the threads out there, choosing the best-layered protection should give you more security and peace of mind.
In conclusion, WAF is great for security in HTTP applications and it is generally used to protect servers. It is aware of web traffic such as HTTP GET, POST, URL, SSL, and more. IPS, on the other hand, provides protection for a wide range of network protocols and can perform raw protocol decoding and find abnormal behavior, but is not aware of the sessions (GET/POST), users, or even apps.
Integrated solutions can be either hardware-based, software, or hybrid. These solutions give you the best of both solutions.







