
Abstract
Knows as Distributed Denial-of-Service (DDoS), this cyber attack attempts to disrupt servers, networks or websites to render them unable of providing resources and services to its users. Typically, the targets for DDoS attacks are “high-profile” targets such as telecommunication enterprises, major cloud service providers, financial institutions and big corporations as well as government agencies and politically related groups. This article will provide an overview on the background and three different types of DDoS attacks and methods for preventing and protecting against said attacks.
From DoS to its advanced form, DDoS attack
The evolution of DoS presents DDoS, an advanced form of a Denial-of-Service attack. Originally, one internet connection or one computer would be used in a DoS attack overloading the systems of the targeted networks by flooding them with excessive external communications requests, in an attempt to temporarily or permanently interrupt services. Once a target is flooded with requests, the site’s host protocol is hit with an exorbitant volume of queues disrupting access to its services and resources. Differentiating factor, a DDoS attack will use multiple distributed networks and computing systems, making it nearly imposible to identify the sources of attacks. Some have referred to DoS as a “zombie attack” and to DDoS as “botnet or zombie army”.
Some may refer DDoS as “botnet”, meaning a group of “zombie computers” or simply a “zombie army”. According to the sources, the present incident rate of DDoS attacks reaches around 30 occurrences per hour. A recent incident many might recall happened in the 2014 Christmas season when the services of Sony Playstation Network and Microsoft Xbox gaming were rendered unavailable. With the networks of both gaming services hit with an overflow from a DDoS attack, users were having difficulty accessing their corresponding networks.
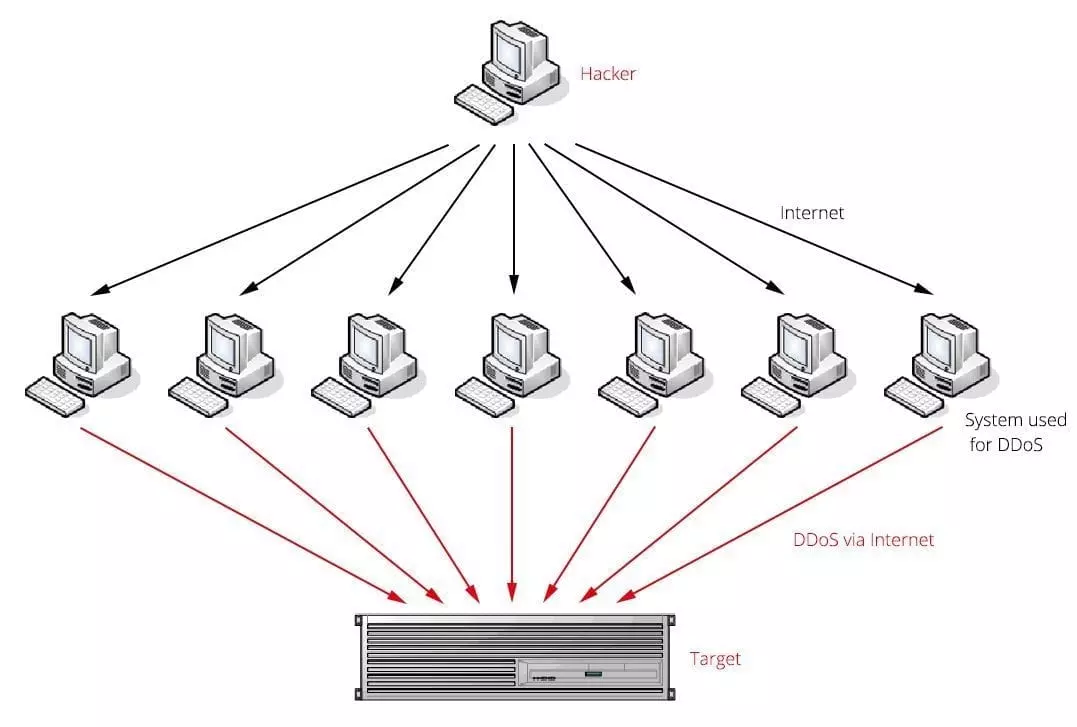
One main objective of DDoS attacks is to flood the network by sending external communication requests, also known as data packets, disrupting it from fulfilling the genuine requests from its users. With the DDoS attack in full spring, the network’s host is being subject to overloaded traffic rendering its services unavailable. Because the intricacy of DDoS attacks is greater than DoS, it of extreme importance to consider common DDoS attack types.
Three Common DDoS Attack Types
1. Network Volume Attack
Aimed at the flooding the traffic of ICMP, UDP and TCP. A possible clue for its detection is when no special public event occurs but there is a huge volume of bps in a short amount of time.
2. Server Protocol Attack
Server resources, including CPU loading and memory space, are actually consumed. Some variations of experienced Server Protocol Attacks include Ping of Death, Smurf and SYN DDoS. An effect of this attack is a high volume of pps in a very short time. There are advancements in modern day operating systems for preventing the majority of attacks to server protocol.
3. Application and System Level Attack
Two popularly known are Slowloris and Zero-day. This type of attack targets web server systems and applications such as Windows, Apache and other HTTP operating systems that are alike, such as OpenBSD. Different from the other two types of attacks, this type of attack uses normal and legitimate requests on the surface. This attack does not use the typical traffic overflow methods, instead with a smaller portion of network traffic it launches web applications like search results or online ordering.
Prevention Measures
Applicable prevention measures include the collaboration of flooding detection, network traffic identification, and defensive blocks against abnormal packets. Implementation of hardware-assisted measures with high performance in deep packet inspection, are a high priority.
Firewall
This is typically the first choice in protection, works great against flood method attacks, many enterprises will implement firewalls set up to deny or allow certain IP addresses, protocols or packets. In situations with intricate DDoS attacks, the firewall must provide a packet filtering function to analyze and categorize any incoming packet as either hazardous, normal or priority.
Intrusion Prevention System
With high processing performance, the IPS can identify traffic and signature patterns, and block abnormal communications requests, minimizing the chances of experiencing overflowing volumes.
Robust Firewall and IPS Systems by Lanner
Standard, traditional firewalls or IPSs alone will not be able to protect against the ever increasing complexity of DDoS. For that reason, Lanner offers powerful and robust platforms, built as ideal implementations for managing industrial and enterprise networks, featuring the following crucial elements:
- Complimentary chipset or PCH to assist CPU coordinating with peripherals. An example is Intel Wellsburg PCH communicating with PCIe lanes, IPMI LAN ports, and storage devices in high efficiency.
- CPU with high processing power to efficiently run deep packet inspections (e.g. Intel® Xeon® E5-2600 series). DDoS attacks with a high complexity can be countered by CPUs with top performance, since they have the ability of handling multiple detection and mitigation tasks.
- A high-port density and 10GbE to 40GbE Ethernet LAN for ultra bandwidth
Considering the technological aspects mentioned above, Lanner’s high-end x86 Rackmount Network Appliance, the FW-8896 is ideal for network optimization, content detection and web traffic filtering. Technological advantages in the platform’s build include the following:
- Intel C612 PCH (codenamed “Wellsburg”) with ultra peripheral connectivity supporting multiple SATA ports PCIe lanes, USB ports and IPMI/OPMA for enhanced peripheral communications.
- Dual Intel® Haswell-EP Xeon® E5-2600 v3 CPUs with C612 chipset supporting DDR4 memory up to 512GB and 40 PCIe 3.0 lanes.
- Dual Intel QPI® links up to 9.6 GT/s
- Up to 8 Ethernet modules with up to 64 GbE ports including 1/10GbE RJ-45 or 1/10/40GbE fiber LAN connectors.
- To optimize packet processing performances, Intel® DPDK (Data Plane Development Kit).
- Acceleration engine Intel® Coleto Creek 8925 and for enhanced cryptographic and compression processes Intel® QuickAssist Technology.
Other than the FW-8896, Lanner Electronics has complete selection of UTM, IPS and firewall x86 Rackmount Network Appliances to protect your network protocols against large-scale DDoS attacks.
