
Abstract
Traditionally, industrial control systems (ICS) like SCADA used to be isolated for its sole purpose of performing mission-critical tasks and controlling the processes within important infrastructures such as oil refinery, power plants, manufacturing factories, water/sewage treatment and energy plants. Therefore, these systems are built with conventional structures and operate in multiple decades of lifespan. However, with the increasing complexity in hardware design and the implementation of open network due to convenience and cost-effectiveness, ICS environments are vulnerable towards cyber threats. There have been incidents of cyber attacks over the past few years and thus ICS security has presented a great challenge. The following will discuss the issue in details and introduce robust platforms that can act as a gateway controller in packet inspection, whitelisting and protocol filtering.
Identifying the Weakness of ICS and SCADA
As mentioned, ICS and SCADA are implemented in segregated environments to control and monitor critical infrastructures. Only authorized individuals have the access to enter these environments. Thus, in traditional ICS design structure, security measures only focused on the physical attack.
However, in recent years, we have heard various incidents of critical infrastructures such as nuclear plants being breached by malicious cyber attacks. One of the most discussed is the Stuxnet which devastated the computing system of Iran’s nuclear plant. Thousands of computers were infected and a widespread damage to Iran’s industrial infrastructure was later reported. It was one of the most evident incidents to prove the apparent vulnerabilities of SCADA system.
There are reports claiming that the vulnerabilities lie in the security-absent structure itself. The reports indicated that hackers usually attack the weak sides of DCS (distributed control systems), PLC (programmable logic controllers) and HMI (human machine interface) through unauthorized remote accesses, non-inspected packets, lack of protocol scanning and filtering as well as loose authentication process. Without proper firewall protection, cyber threats will bring devastating results.
It is perhaps necessary to look into reasons why traditionally-reliable SCADA and ICS systems become vulnerable and weak against cyber threats:
1. The increasing dependence on the Internet.
Organizations and enterprises today are largely dependent on the Internet technology for their business operations, especially the multinational ones. The convenience of the Internet provides easy solution to bridge corporate networks and on-site facilities (such as smart grids) together. However, that means more network accessing points have to available and it opens up more loopholes for data breaches. In other words, Internet provides organizations easy operating solutions but also offers easy targets for potential hackers.
2. The increased use of commercially off-the-shelf operating systems
Organizations and enterprises rely largely on commercially off-the-shelf operating systems for flexibility, scalability and cost-efficiency. Indeed, this type of commercial operating system offers an easy and cost-effective approach for network integration and provides an easier transition for the training of network traffic administrators. However, the wide availability of such operating systems actually induces more potential cyber attacks as many intruders are quite knowledgeable about these systems. In other words, cyber attackers are already very familiar with these operating systems.
3. The increased public exposure
Nowadays, many of the critical infrastructures come with an official website accessible to the general public, no matter for educational or legitimacy-related purposes. In fact, some even release documents like papers, reports and some financial information. The increased public exposure indeed attracts data intruders to breach the SCADA and ICS systems.
4. Man-made causes
Man-made factors may arise from internal causes. Traditionally, errors may occur due to improper design, installation, configuration or operation, if the on-site staff was not well-trained. This is considered as one of the internal causes. However, nowadays, with the wide availability of communication technologies, internal issues must take unsecured devices including PCs, laptops, smart mobile devices and USB peripherals into considerations.
Establishing a Solid Industrial Security
In order to establish a solid industrial security, aside from software implementations, it is necessary to build a powerful and robust hardware platform. The gateway controller must filter the protocols, such as access detection, packet inspection, white-listing, and network traffic monitoring. Also, the gateway controller must be able to operate under demanding environments as critical infrastructures are usually located in remote, harsh areas such as power substations, nuclear plants and manufacturing plants.
As illustrated in the diagram below, robust industrial gateway controllers (namely LEC-6020B/LEC-6020C) are placed between PLCs/HMIs/DCS and the main control center of the infrastructures. These controllers must be IEC 61850-3 compliant in order to perform their functions in challenging conditions. The compliance mainly requires the following:
- Shock and vibration resistance: must meet the standard of resistance at 50G of shock and 5-to-500MHz for vibration.
- Wide range of operating temperature from -40℃ to 75℃.
- EMC test certified.
Aside from environmental robustness, a solid security addresses the needs of a comprehensive cyber security for PLCs/HMIs/DCS, and even to corporate networks. In the diagram below, LEC-6020B/LEC-6020C act as the gateway controllers to perform white-listing, protocol filtering, and access detections for the networks that bridge PLCs/HMIs/DCS with the infrastructure. These gateway controllers will deeply inspect the packets traveling through its monitored network protocols. In addition, these control platforms can be programmed to conduct white-listing, which restricts the access to unrecognized individuals. In that case, the protocols are protected against unauthorized applications and even potential malware that might devastate the whole operations.
At device levels, the LEC-6020 models in the diagram are built with ESD and surge protection to perform their functions reliably in any demanding environment. In addition, these gateway controllers offer BIOS Lockup to prevent themselves from being accessed by unauthorized individuals to tamper platform configurations. To offer a higher level of device security, LEC-6020 models support TPM* (Trusted Platform Module) function to protect themselves from unauthorized accesses to the hardware.
For emergent backup, the LEC-6020s in this scenario support LAN Bypass. In the event of a failover to one of the systems, another LEC-6020 will function as the backup gateway for data packets to travel through.

In a more sophisticated implementation, owners of critical infrastructures may also adopt the use of LEC-6230 as shown in the diagram below, a powerful cyber security appliance with both IEC 61850-3 and IEEE 1613 compliances. In this scenario, LEC-6230 acts as the main control center to perform encryptions while LEC-6020s will function as the decryption stage.
With encryption, data and information flowing in this protocol will be “transformed” into meaninglessly unreadable random logs to those without the decryption key. In other words, the data or information is “encrypted” to those without the ability to decode it. This will secure the transmission among devices in ICS and SCADA systems. When the encrypted data travels to LEC-6020, the data would be decrypted before it travels to PLCs/HMIs/DCS. During the encryption and decryption process, LEC-6230 acts as the top administrator and the whole system is being “watched” for any abnormal network event happening.
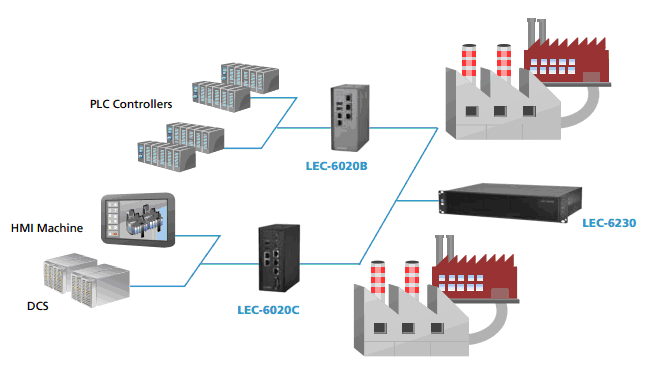
From the discussion above, solid cyber securities require a comprehensive platform at different levels. At the fundamental level, multiple gateway controllers like LEC-6020s are implemented to filter the protocols and deeply inspect the packets for PLCs, HMIs, and DCS. These controllers must be IEC 61850-3 compliant and support security functions such as TPM*, BIOS Lockup, ESD/surge protection and LAN Bypass. For a more sophisticated and thorough application, LEC-6230 shall be deployed to run encryption processes and control all the on-site LEC-6020s. In that case, LEC-6020s will perform the decryption tasks. With encryption and decryption, the data traveling through the protocols can be secured and unreadable to those with the decoding key. This will then build up a solid cyber security.
*TPM function is optional and may require custom designs.





