As we know, with the rise of IoT and explosion of networked devices, cyberattacks have grown substantially. This wide range of threats means that network security teams cannot leave anything to chance or luck. They should always be up to date in terms of the latest cyber security technologies available to them for protecting the network at different levels. We regularly relate the protection of the network with certain specific software-based solutions such as Firewalls, NGFW, IPS, IDS, antivirus or antispyware to name a few. However, considering hardware level security features is becoming increasingly critical in the software-defined everything world.
In this article, we will discuss two very useful hardware based cyber security technologies that are becoming increasingly important features of cyber-hardened network appliances for security and SD-WAN applications. We are talking about TPM (Trusted Platform Module) and Intel PTT (Platform Trusted Technology) or TPM 2.0. Before we do a comparison, let’s quickly discuss what each of these technologies are.
TPM (Trusted Platform Module)
TPM stands for Trusted Platform Module, and it is a microchip designed for the security of computers using encrypted keys. These are stored in the TPM chip that is located on the computer’s motherboard. Most current security solutions are based on software. As a result, they do not provide sufficient security protection and are vulnerable to physical or logical attacks. However, TPM is a security solution based on hardware and software. Unlike many other information security defense options, TPM is a popular feature in endpoint security and network edge computing systems.
This chip stores RSA encryption keys specific to the host system for hardware authentication. Each TPM chip contains a pair of RSA keys called Endorsement Key (EK), which are inside the chip and cannot be accessed by the software. This key pair is generated by the TPM chip based on an approval key and a specific owner password. When a user takes control over a computer, the Storage Root Key (SRK) is generated.
When the system software generates a key or certificate, the key or certificate is sealed in the TPM. In other words, the TPM chip is a “safe” where we store encrypted data keys.
Using TPM on our computer allows us to manage information such as:
- Digital certificates.
- Local administrator passwords.
- User folders with administrator passwords.
- Log protected with administrator passwords.
- User passwords.
- Hard disk encryption passwords (HDD).
- SNMP and Web server passwords.
- Remote Control Passwords.
A great advantage of TPM, is that it uses its internal firmware so it is free of software-based attacks with the operating system. So this adds one more layer of protection increasing the security of our data. It can also be used to work in conjunction with other hard disk encryption applications as well as for the storage of identification data such as fingerprints.
But TPM is not only limited to generating and storing encryption keys safely, but it can also protect a computer from the moment the booting process. Using a system called Core Root of Trust Measurement (CRTM), Platform Configuration Records (PCR) are created. Using several PCR’s, different records of the state of our computer are taken and a quick review of the equipment can be made before the operating system starts, even canceling the operation or avoiding software updates in case of finding some anomalies or inconsistencies in the state of the computer system.
TPM 2.0
TPM has been evolving towards TPM 2.0, which is a new approach that is no longer oriented towards the need to have a dedicated hardware on the motherboard but using the processor more and relying more on the firmware, where making libraries available will enable the options that apply to the platform we are using. Thanks to this evolution, there are now solutions that bring TPM to even more devices in more fields such as industrial processes and automotive solutions. Let’s talk about an example: Intel PTT.
Intel introduced PTT (Platform Trust Technology) in 2013 as a firmware-based solution that uses the same main processor of the computer. This allows more devices from a lower range and lower power consumption to enjoy the Core Root of Trust Measurement (CRTM) concept that hardware-based TPM devices have.
TPM 2.0 enabled crypto security is especially important for industrial communication gateway and industrial cyber security devices. TPM 2.0 along with LAN Bypass technology offer robust hardware level cyber-hardening at low power consumption.
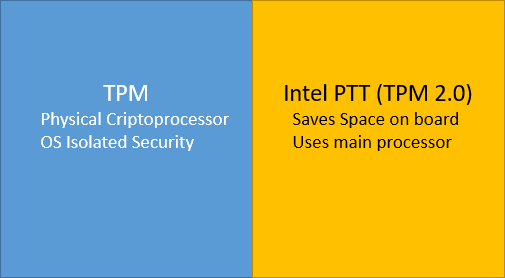
TPM Network Appliance examples
Lanner offers TPM and TPM 2.0 adding an extra layer of security to the data. Here are some examples of Lanner platforms:
NCA-5520
The NCA-5520, powered by Intel®’s Xeon® Processor Scalable Family and Intel® C626 or C621 chipset, features optimized computing power and virtualization capacity in a compact 1U form factor with support for up to 384GB DDR4 system memory at 2666 MHz. Optional TPM Support. It delivers a multitude of advanced networking features for maximizing packet processing efficiency and cryptography acceleration.

NCA-1515
A desktop network appliance powered by Intel® Atom® C3000 (codenamed Denverton) CPU, features robust performance and Intel’s QuickAssist Technology, offering cryptographic acceleration and commercial-grade LAN functions in a 231mm x 200mm x 44mm (WxDxH) form factor. 4x GbE RJ45 Intel® SoC Integrated MAC, 2x GbE RJ45 Intel® i350 (by SKU) and 2x GbE SFP Intel® i350 (by SKU). 2x 260-pin SODIMM (by SKU), DDR4 2400/2133/1866MHz ECC SODIMM, Max. 32GB. 1x RJ45 Console, 2x USB 2.0, 1x Onboard EMMC 8G, 2x Nano SIM for M.2. 2x Mini-PCIe (PCIe / USB 2.0), 1x M.2 2242 B Key (USB 3.0). TPM 2.0.
In conclusion, although the TPM technology is still in development, the need to increase the security of network users in an integral and transparent way, we will surely see this solution in more and more appliances. If you are thinking seriously about increasing the security of your data starting with the endpoint equipment, why not look for devices that already have this convenient feature integrated?






