
The use of Industrial Control Systems (ICS) stretches across a wide range of critical infrastructure sectors, including energy, manufacturing, transport, water and waste management. ICS traditionally were isolated systems to control and manage industrial assets, machinery and systems. However, that is changing as we enter the age of fourth industrial revolution or the Industry 4.0 era. Now as the information technologies (IT) and operational technologies (OT) are converging into an integrated network for innumerable benefits, vulnerabilities that come embedded into the ICS components have much more exposure to the known and unknown cyber threats.
Which Industrial Control Systems have vulnerabilities?
The answer is, almost all of them. The top three industrial control system components known for having most vulnerabilities are human-machine interfaces (HMIs), electric devices such as power analyzers and relay platform units, and Supervisory Control And Data Acquisition systems (SCADA). Some of the vulnerabilities are common between almost all ICS components. We will be reviewing the ones that definitely are among the top ones. Let’s take a look.
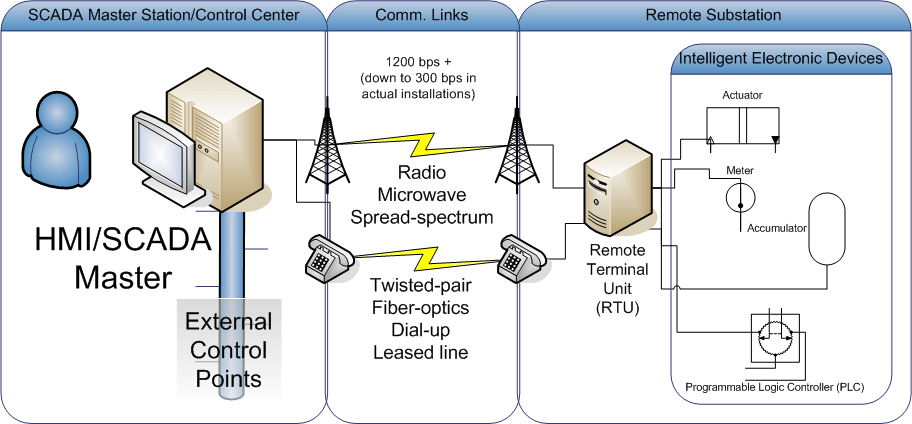 Overview of Industrial Control System Components used in Substation Automation
Overview of Industrial Control System Components used in Substation Automation
Here are 5 Common Vulnerabilities
1) Buffer Overflows
Buffer overflows are programming errors that cause software code to overrun the boundary of the buffer they override adjacent memory blocks. These kinds of programming errors are why input validation processes exists as they can crash the program, cause corrupted data, or allow for the execution of malicious code within the system. It is therefore essential that the correct testing and validation methods as well as any appropriate boundary checks are made so as to ensure against buffer overflow or software failures. Poor input validation can also leave industrial control systems such as SCADA, HMI, PLC´s and DCS open to other forms of cyber attacks such as SQL injections, in which malicious code is embedded in applications then passed to the backend database so as to produce query results that wouldn’t be provided under normal circumstances. Or cross-site scripting, where attackers inject client-side scripts into web pages, often with the goal of bypassing access controls.
2) Unauthenticated Protocols
In industrial control systems, authentication protocols are used to transfer authentication data between two entities so as to authenticate both the connecting entity and itself. Authentication protocols are the single most important layer of protection for communication with computer networks. When an industrial control system’s protocol lack authentication, any computer or device connected to the network can input commands to change, alter or manipulate the operations being controlled by the ICS. In the example of the German steel mill hack mentioned earlier, unauthenticated protocols could very well have led to a similar result and efforts should be made by industrial organizations to map out the remote access points in their systems and look to provide and implement adequate security resources and practices in order to decrease the risk posed by unauthenticated protocols.
3) Weak User Authentication
As we mentioned above, authentication is the process of proving the identity of users on a network or system. A weak user authentication system would be an authentication process that is easily beaten or bypassed. For example knowledge-based authentication, which works on authenticating users based on knowledge only they would know such as passwords, can be incredibly weak as password management and policies aren’t kept up-to-date or regularly changed.
Identity-based authentication systems, on the other hand, can be very strong user authentication systems as they typically work on biometric readings such as a fingerprint or iris scan. These biometric readings are much harder to imitate or bypass than knowledge-based systems, which could theoretically be cracked with nothing more than a good guess. It is, therefore, essential that businesses recognize the value of their assets and provide strong user authentication systems to suit.
4) Untimely Adoption Of Software
The untimely adoption of software may not be the first thing many people think of when considering the vulnerabilities to industrial control systems, but the improper set up of untested software can cause holes to appear in control system set ups and, eventually, lead to their exploitation from malicious hackers if the software isn’t reconfigured in the correct way. The improper implementation of patches can also cause further issues and become a detriment to the optimal running of industrial control systems. Before implementing any new software or patches, organizations could create checklists in order to verify the functioning of technology to regulatory requirements as well as ensure that any pending implementations where ready to perform a the required level.
5) Poor Password Policies or Management
One of the most obvious vulnerabilities to any computer, network or industrial control system is poor password management.
As simple as it may sound, an unbelievable number of businesses and organizations still underestimated the power of decent password management as a means of protecting themselves from cyber attacks. While the convenience of using a password that you know and use for other online accounts may be tempting, the risk such scenarios entail is never worth the few seconds you save inputting a weak password. Sometimes, passwords may be too vulnerable in themselves and business that feel it necessary could opt for even more stringent authentication processes using identity-based systems to read biometric user data as a replacement for passwords altogether.
Conclusion
There were 19 known vulnerabilities to industrial control systems in 2010, in 2015 that figure has rose to 189. As yet, we can’t be sure how that number has changed over the past two years, however, what we can be sure of is that the threats to ICS will continue to grow as adversaries gain a more advanced knowledge of these systems as well as access to better hacking equipment.
Our reliance on industrial control systems to drive the technologies that make our lives better will only produce more and more of them. ICS component manufacturers will have to keep up and quickly spot the vulnerabilities and resolve them. We may also see more embedded security coming into the industrial control systems in future. Close collaboration and continuous cross communication between critical infrastructure authorities, cyber security software developers and the ICS hardware OEM´s will be required in order to beat the tools of sophisticated attackers.
A robust ICS Cyber Security system stands between a chaos and a cyber attack, and since all of the critical infrastructures relies on the ICS systems, it is therefore imperative on the industries and relevant government bodies that comprehensive compliance procedures are updated regularly to keep up with evolving threats.








